Reverse Proxies
To facilitate the unified management and distribution of SSL certificates, service expansion and access to off-the-shelf gateway services, we provides several configurations for configuring reverse proxy services to the gateway.
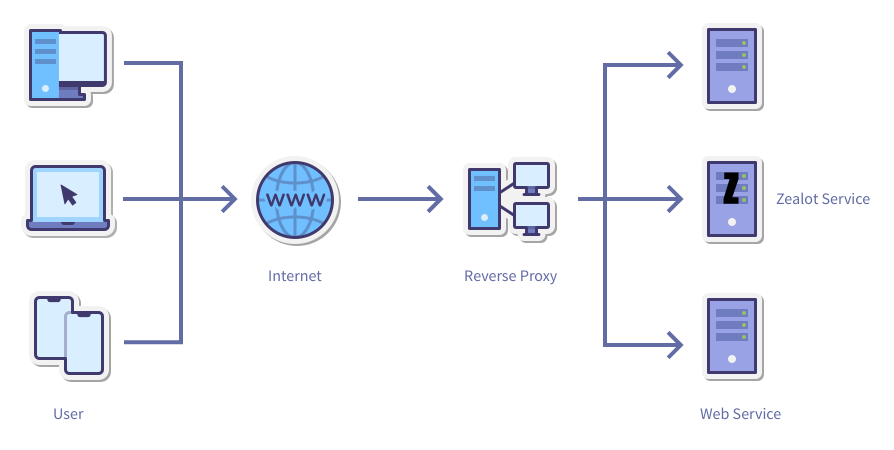
Prepare
The following data needs to be prepared to configure the reverse proxy:
| Name | Sample value | Description |
|---|---|---|
| Domain | zealot.example.com | |
| Reverse proxy service IP address | 172.16.56.1 | |
| Zealot IP address | 172.16.56.100 | Reverse Proxy can be accessed Change to 127.0.0.1 Reverse Proxy and zealot with one host. |
| Zealot public port | 8901 | Reverse Proxy can be accessed |
| Zealot internal port | 80 | No need modify |
| Let's Encrypt Email address | your-email@example.com |
Traefik
Traefik is an open source reverse proxy and load balancing tool, which provides a variety of Providers can achieve access to the reverse proxy and configure the SSL.
Configuration
Regardless of the type of Provider used the core configuration items are the same and constitute the reverse proxy service configuration consists of three main components: discovery port number, routing rules (including access port number, domain name binding and SSL)
Traefik service
- yaml
- toml
- cli
entryPoints:
web:
address: ":80"
websecure:
address: ":443"
certificatesResolvers:
letsencrypt:
acme:
email: your-email@example.com
storage: acme.json
httpChallenge:
entryPoint: web
[entryPoints]
[entryPoints.web]
address = ":80"
[entryPoints.websecure]
address = ":443"
[certificatesResolvers.letsencrypt.acme]
email = "your-email@example.com"
storage = "acme.json"
[certificatesResolvers.letsencrypt.acme.httpChallenge]
# used during the challenge
entryPoint = "web"
--entrypoints.web.address=:80
--entrypoints.websecure.address=:443
--certificatesresolvers.letsencrypt.acme.email=your-email@example.com
--certificatesresolvers.letsencrypt.acme.storage=acme.json
--certificatesresolvers.letsencrypt.acme.httpchallenge.entrypoint=web
Docker
Enable Docker provider then edit the Docker Compose file:
version: '3'
services:
zealot:
<<: *defaults
labels:
- "traefik.enable=true"
- "traefik.http.services.zealot.loadbalancer.server.port=80"
- "traefik.http.routers.zealot.service=zealot"
- "traefik.http.routers.zealot.rule=Host(`zealot.example.com`)"
- "traefik.http.routers.zealot.tls=true"
- "traefik.http.routers.zealot.tls.certresolver=letsencrypt"
- "traefik.http.routers.zealot.tls.domains[0].main=icyleaf.dev"
- "traefik.http.routers.zealot.tls.domains[0].sans=zealot.example.com"
# Comment port, no need to public
# ports:
# - "8901:80"
network:
# Change the network what traefik service is
- traefik-services
networks:
# Change the network what traefik service is
traefik-services:
external: true
Deployment with Docker is limited to Traefik and Zealot service are usually in the same OS system of the same machine, cross-machine can not achieve communication, for cross-machine need to refer to the following two configuration options.
Consul
Enable Consul provider or Consul Catalog provider, add key-value below:
consul kv put traefik/http/services/zealot/loadbalancer/server/port 5
consul kv put traefik/http/routers/zealot/service zealot
consul kv put traefik/http/routers/zealot/rule 'Host(`zealot.example.com`)'
consul kv put traefik/http/routers/zealot/tls/certresolver letsencrypt
consul kv put traefik/http/routers/zealot/tls/domains/0/main icyleaf.dev
consul kv put traefik/http/routers/zealot/tls/domains/0/sans zealot.example.com
Nomad
Enable Nomad provider and make sure Nomad version >= 1.3:
job "zealot" {
datacenters = ["dc1"]
type = "service"
group "zealot" {
count = 1
network {
port "http"{
static = 80
}
}
service {
name = "zealot-http"
provider = "nomad"
port = "http"
}
task "server" {
driver = "docker"
config {
image = "ghcr.io/tryzealot/zealot:nightly"
ports = ["http"]
args = [
- "traefik.http.routers.zealot.rule=Host(`zealot.example.com`)",
- "traefik.http.routers.zealot.tls=true",
- "traefik.http.routers.zealot.tls.certresolver=letsencrypt",
- "traefik.http.routers.zealot.tls.domains[0].main=icyleaf.dev",
- "traefik.http.routers.zealot.tls.domains[0].sans=zealot.example.com"
]
}
}
}
}
Caddy 2
The configuration only needs to relate the ip part after tls and proxy:
:443
log
# Use Let's Encrypt service
tls your-email@example.com
reverse_proxy 172.16.56.100:8901
Nginx
The following is the general configuration, if not effects welcome to file a issue:
upstream zealot {
zone upstreams 64K;
server 172.16.56.100:8901;
keepalive 32;
}
map $http_upgrade $connection_upgrade {
default upgrade;
'' close;
}
server {
listen 80;
listen [::]:80;
server_name zealot.example.com;
location /.well-known/acme-challenge/ { allow all; }
location / { return 301 https://$host$request_uri; }
}
server {
listen 443 ssl http2; # Optional: http2 may needs install extension
listen [::]:443 ssl http2;
server_name zealot.example.com;
ssl_certificate /etc/certs/zealot-cert.pem;
ssl_certificate_key /etc/certs/zealot.pem;
# Optional
# ssl_ciphers HIGH:!MEDIUM:!LOW:!aNULL:!NULL:!SHA;
# ssl_session_timeout 5m;
# ssl_session_cache shared:SSL:1m;
# ssl_prefer_server_ciphers on;
location / {
proxy_pass http://zealot;
proxy_redirect off;
proxy_pass_header Authorization;
proxy_set_header Host $host;
# proxy_set_header X-Forwarded-Ssl on; # Optional
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection $connection_upgrade;
client_max_body_size 0;
proxy_read_timeout 36000s;
}
}
And you need update max body size in http block. Recommended is 200MB, if it's a game,
50% more can be played to make a surplus according to the actual file size.
http {
[...]
client_max_body_size 200M;
}